Cybersecurity & Pentesting
CIS Benchmarks
Completed in 6 Days, Not 6 Weeks
Securing Additive Manufacturing Infrastructure for the Client
The client powers leading additive manufacturers like Boeing, Ricoh, and Vast Aerospace with FLOWS, a digital platform for managing materials, operations, and compliance. Their enterprise clients demand infrastructure that is secure, compliant, and reliable from the ground up. To meet these expectations, the client expanded their offerings to include Red Hat Enterprise Linux (RHEL) and required the underlying system be fully hardened.
The Challenge
The client needed to move fast while meeting strict security benchmarks. The project scope included:
Hardening RHEL to CIS Benchmark Level 1
Remediating CAT I and CAT II security findings
Converting existing Ubuntu-based Ansible automation to support both RHEL and Ubuntu
Automating all tasks using clean, testable playbooks
Timeline: 7 days. Delivered: 6 days.
How Space-Rocket Helped
Michael executed the full RHEL Security Hardening and Automation Conversion project independently, with regular Slack check-ins mapped to milestone deliverables.
RHEL Security Hardening
Provisioned and configured RHEL instances
Applied CIS Level 1 controls across system settings
Hardened sshd_config and disabled root SSH access
Configured SELinux for general workloads
Removed unnecessary services and tightened default permissions
Addressed all CAT I and CAT II findings via automated Ansible tasks
Dual-Platform Ansible Automation
Refactored playbooks originally built for Ubuntu
Built platform-aware logic using Ansible conditionals
Migrated package and service tasks from apt to yum/dnf
Isolated OS-specific vars and templates
Ensured parity with original behavior through functional tests on both platforms
Tooling and Validation
Developed an Ansible role to install Kubernetes components and verified install state
Confirmed system integrity post-provisioning
Validated all playbooks on fresh RHEL hosts
Compliance and Documentation
Delivered full Ansible codebase with RHEL and Ubuntu support
Provided operational documentation and role-level descriptions
Created setup instructions, testing notes, and hardening checklists
Verified compliance with enterprise security expectations
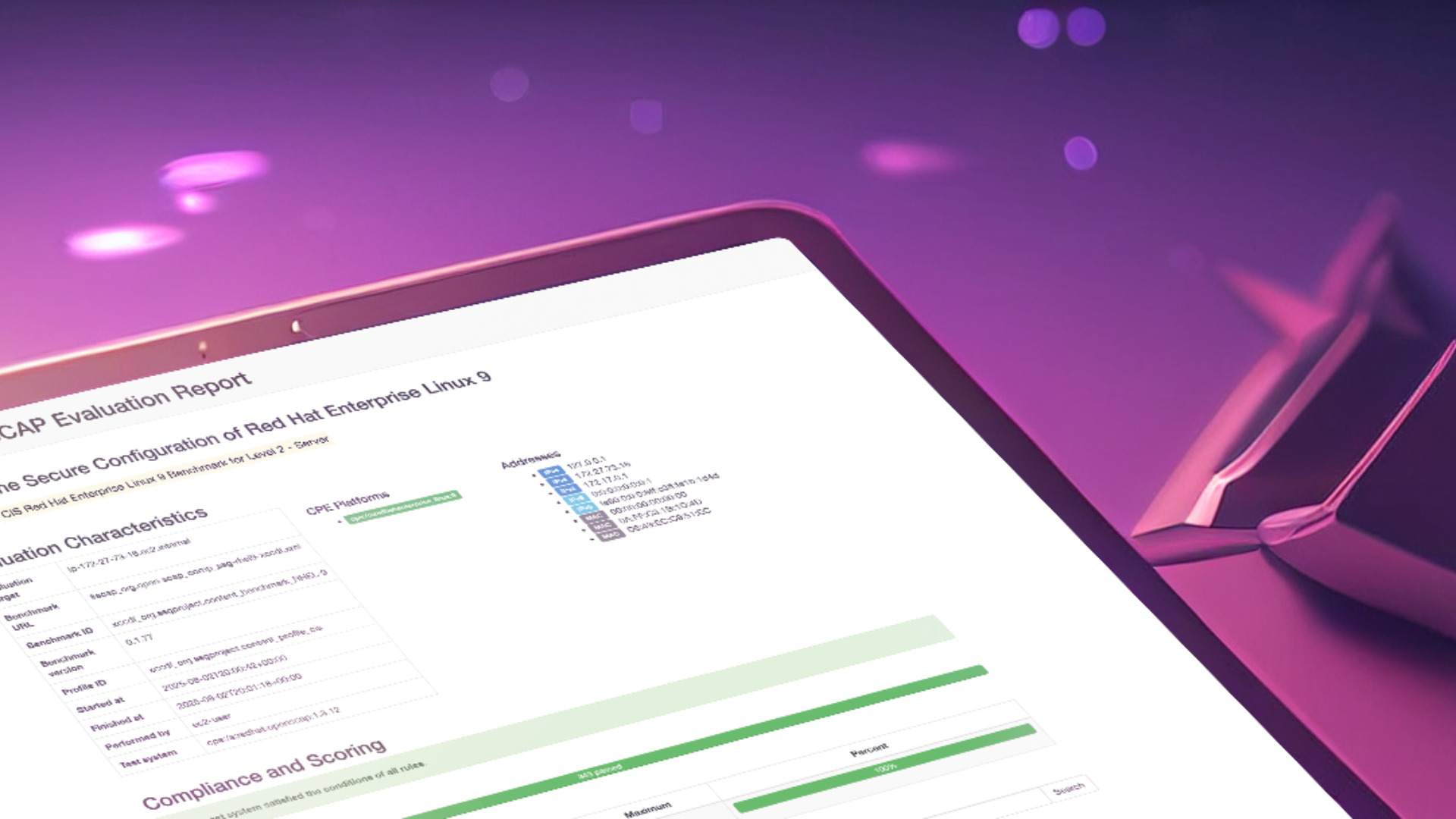
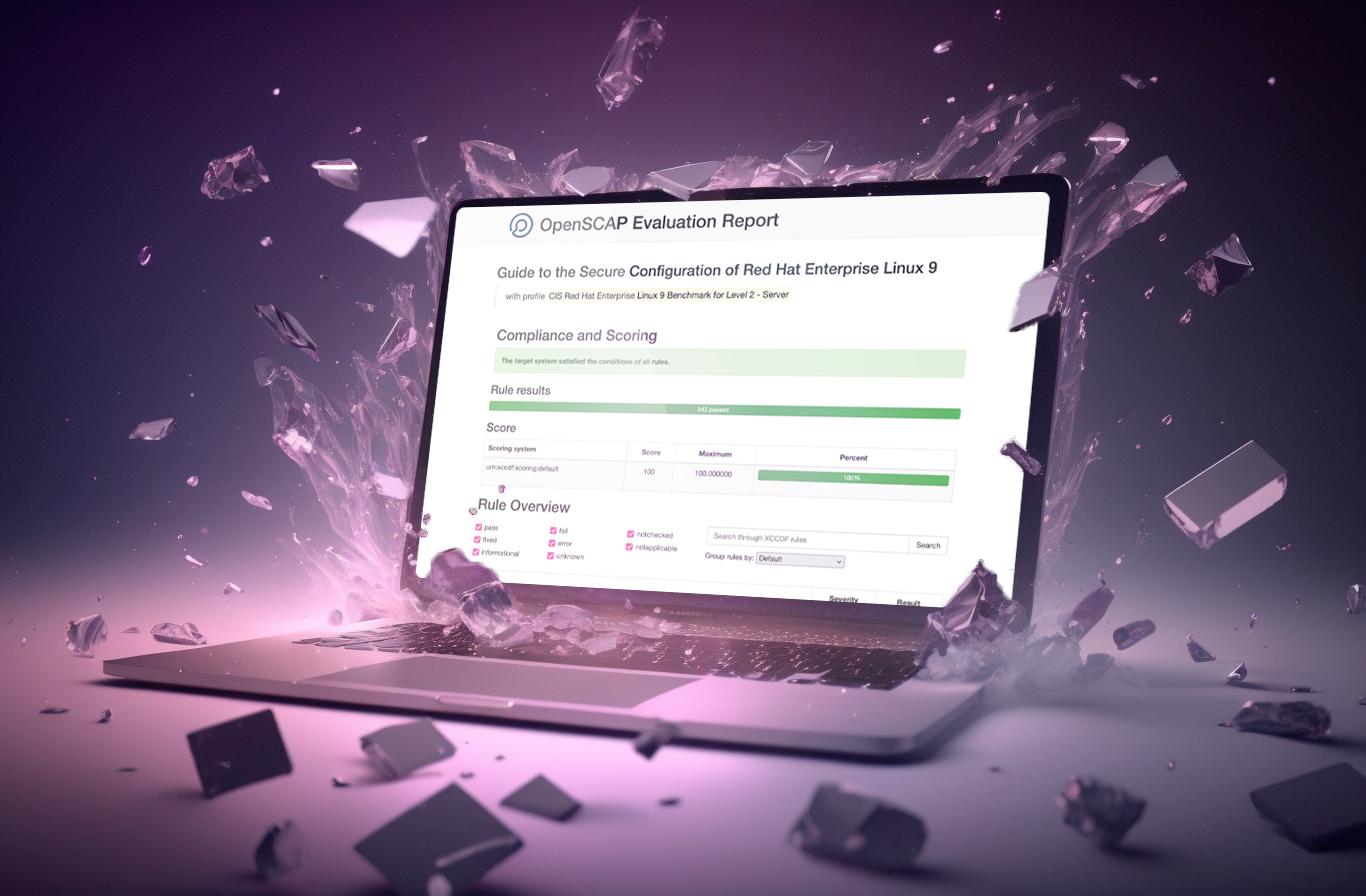
OSCAP scans to confirm CIS Benchmark compliance
Outcome
In just 6 days, the client received:
A security-hardened RHEL environment
A dual-platform Ansible automation framework
Complete CIS Level 1 alignment and CAT I / II remediation
All supporting documentation for handoff and continued use
The client now runs on a hardened, maintainable infrastructure designed to meet the needs of their most security-conscious customers, delivered ahead of schedule and ready for production use.
Project Details
Need similar services?
Agencies providing cybersecurity & pentesting
Posted this
S
Building innovative web solutions from San Francisco
C
Empowering Business Security and Compliance
T
Build Better Software
M
We take care of all your technology needs, so you don’t have to.
G
Protecting websites and businesses from cyber threats
C
Transforming education through innovative IT solutions
T
Transforming Digital Excellence through Innovation and Performance
N
Umbraco CMS / web design and expert .NET Development Agency
B
Expert IT Solutions for Small Businesses
O
A Digital Transformation & ISO Certified Company
E
Building Innovative Solutions for a Brighter Tomorrow 🌞